I would agree with you if there were a simple way to tell what the USB-C cable I have in my hand
https://caberqu.com/home/39-ble-caberqu-0611816327412.html
This would do it.
Nope. I don’t talk about myself like that.
I would agree with you if there were a simple way to tell what the USB-C cable I have in my hand
https://caberqu.com/home/39-ble-caberqu-0611816327412.html
This would do it.
I killed it from task manager though.
“End task”
No, but you’ve stated something that’s factually not true. And with all the shit that’s streamed on the internet, this is nothing near “weird”.
Sorry that you don’t know what you’re talking about.
over 3 hours and 20 minutes now by the way… Explorer.exe hasn’t restarted. What you claim has NEVER been the behavior.
Edit: I’m killing the stream. It’s been over 4:20… I think the point is proven. Still no explorer.exe. Because when you kill the process, it does not restart.
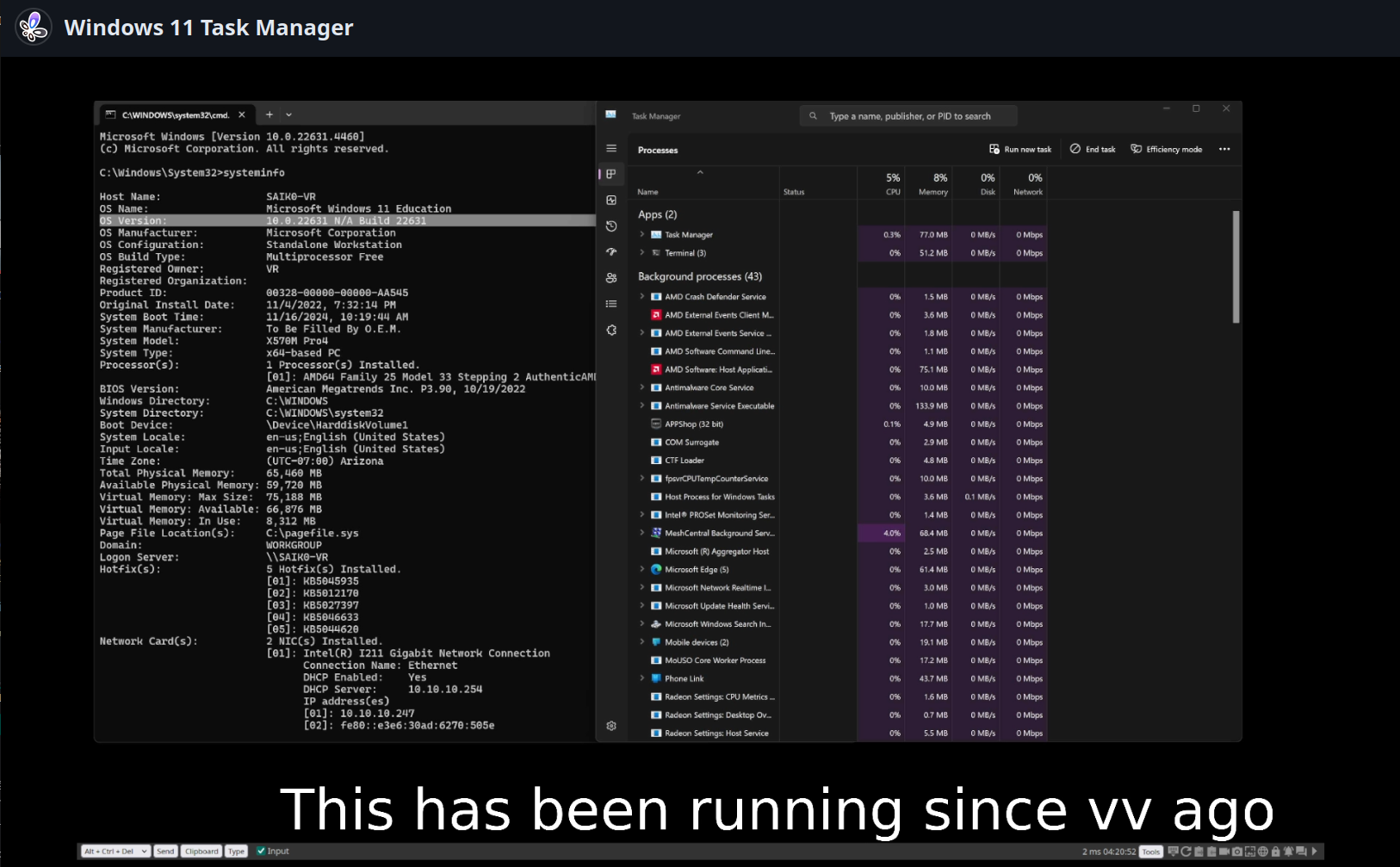
No. It’s not. I spun up a vm and killed explorer.exe. How long should I be waiting? Cause I"m several minutes in and explorer hasn’t restarted itself yet. Also tested it on my VR computer (only non-linux physical machine in the house).
Here I’ll even stream it for you. <removed>. I kill the process at basically 16:00(MST) it’s been 5 minutes now and the stream is going.
Edit: Over 19 minutes now… Still waiting for it to restart…
Edit2: Over an hour now… Still waiting for it to automatically restart. BTW the machine is windows 11. Latest patch/update.
Edit3: pulling the stream. Ran it for over 4 hours. The point is proven. It doesn’t restart itself.
If you kill explorer.exe manually it doesn’t respawn. You have to star the process yourself again.
Unless something changed in the past year.
Anything that hooks into explorer.exe tends to require windows to reboot.


Yes. But there are lists of well known IPs that are serving DoH. So you can just block those. Obviously blocking 443 is not a good idea.


So am I. I’m not sure what you think wasn’t relevant. It’s a literal DoD spec. Yes that spec is outdated, but it’s still in Dban.
You coming out of nowhere talking about how the DoD spec itself is “dead” doesn’t change the fact that it’s available and probably still used by many people out there. I’m willing to be that several companies have the old DoD spec embedded in their own SOPs. And I was always talking in the context of the contract work I did long ago which WAS to the old DoD spec regardless.


Block all port 53 traffic from your network outside of your DNS server/pihole itself.
Block all known DoH servers.
If you want to get REALLY fancy you can write a NAT rule that will force any outgoing request on port 53 to route to your dns/pihole.
I do all of this. It’s actually funny to see the requests that were hardcoded to go somewhere. Giant fuck you to those companies.


That was basically the workflow. On smaller drives you could do one when you get in, one at lunch and one before you left. Eventually drives got large enough that it was just once in the morning and once before leaving.
I’ll overdo it.
Half the contracts you didn’t know if they wanted the short wipes or long wipes. So you just do long wipes to cover your ass. It’s not like there was a rush, it was a simply menial task that became a second nature set of bashing the keyboard. Like typing some of my passwords and pins… I have no fucking clue what they are anymore… but put in front of the keyboard and I can type them by muscle memory.


I think the issue comes down to whether the org in question does that 7 passes consistently on all discs, or if it just so happened to start that policy with those that had evidence on them.
No? If 1 is sufficient, any additional shouldn’t matter in any considerations at all. Could have simply been somebody who hit the preset on accident.


Congrats? DBAN was made prior to 2006… IT people existed before 2006. What’s your point? You think that people just spawned into existence in 2006 with decades of IT knowledge? So like I said… “It WAS my default for a very long time because I simply defaulted to it for COMPLIANCE reasons”… eg. my contracts at the time required it and I ran boatloads of wipes.
Regardless… DOD 5220.22-M now states
The National Industrial Security Program Operating Manual (NISPOM) is now Part 117 of Title 32, Code of Federal Regulations.
So let’s go look at the NISPOM stuff which says… NOTHING! So what you end up with is companies referencing the old DOD 5220.22-M because old government contracts will actually say that specific document in contracts as something that must be adhered to for a long long time. So even though it “died” on 2006, contracts may not be renewed for some time after that which still keeps the document alive.
Now DOD 5220.22-M actually specified and defines short wipes (3 pass) and long wipes (7 pass). And in theory, could be superceded by NIST 800-88 (and probably is the default on modern contracts). And regardless of all of that… DoD internally has it’s own standards, which after wipe often requires degaussing or outright destruction of the disk, I remember having a dedicated device for it that would document serials and stuff. I’d have to pull up my army documents to remember which specific rules required that type of stuff, but I’m not going to dig out shit from 2010 just to argue with someone on lemmy.
So I guess this boils down to… The world didn’t spawn into existence in 2006. People are older than 2006 and are allowed to talk about their experiences from before the “old times”.
Edit: And in current contracts… all our shit is NVMe and secure erase. But I’m willing to bet muscle memory would still kick in for me if I saw the DBAN screen.


so someone using it is being very intentional.
Not if you’re used to taking DoD requests. It was my default for a very long time because I simply defaulted to it for compliance reasons.
It’s also considered wildly overkill
Absolutely is. Doesn’t mean that people like me aren’t out there in droves.
But SSDs make this all moot and HDD are being phased out of many environments. SSDs with chucking the key is more than sufficient as well.


It is… It’s literally a preconfigured option on the dban selection list.
Source: My memory… but if that’s not good enough, here’s wiki too.
https://en.wikipedia.org/wiki/Darik's_Boot_and_Nuke
and DOD 5220.22-M (7 passes) are also included as options to handle data remanence.


At this point I’d argue it’s more convenient anyway. Most flavors install quicker and simpler than windows. It runs faster due to less bloat and bullshit. For the vast majority of people on this planet who only ever need to get to a browser. It’s a better experience. Just one they wouldn’t be familiar with so they’re “scared” to try it.


Depends if you like getting yelled at by an AI hologram about not learning things.
Ignoring the CD rom addition thing… cause that made the console look like a toilet, and I never had one.
Wolf/Doom on it was pretty unique and great ports for what it was.
Tempest 2000 was good
And AVP was good.
That’s what I remember. I didn’t have every game. I know games like Rayman were received well on the console.
It wasn’t a completely shit console… Just needed more games… and possibly to cut costs somewhere. Cause it was expensive at the time, being a full 25% more expensive than the SNES (with a MUCH larger library) and 30% more than the Sega Genesis (with a MUCH MUCH larger library). They worried too much about specs rather than making/getting good games on the console.


That’s a completely fair assessment. They’re definitely still quite expensive.
But I already have a 7950x3d and a 7900xtx… My machine is as good as it’s getting. I had the budget, and have some needs that the larger screen meets.
Has it been worth it? Eh… situationally it’s been super nice. But I can’t say it’s been worth the extra $600 I paid above the next flagship spec quite yet. My first samsung fold though… Verizon paid for me previous phone and paid me more than I paid for it… So that one was definitely worth it.


No. The implication of my “comfortability” with google holding my credentials is that they can use it, or leak it. You wouldn’t know that they did it. I said I don’t trust them, you said “if google did pull something”, I’m saying you wouldn’t even know if they DID pull something. They control such a vast amount of infrastructure and resources that they could do a boatload of malicious stuff and you’d never know. Hell they do some quite malicious things with AMP, ads, pushing nonstandard shit in chrome, etc… But you do you. Give them all your shit. They won’t complain. But you won’t catch me in that boat.


Put all your normal stuff into a profile and leave the work app on the primary profile. They will be separated.
That aliexpress device doesn’t tell you what wattage or data speed the cable will max out doing. Just what wattage it’s currently doing (to which you’d need to make sure that the device you’re testing with on the other side is capable and not having it’s own issues). Also can’t tell you if the cable is have intermittent problems. If all you care about is wattage, then fine. But I find myself caring more about the supported data speeds and quality of the cable.
But yes, I agree that cables should just be marked what they’re rated for… However it’s possible well built cables exceed that spec and could do better than they’re claiming which just puts us in the same boat of not really knowing.
Edit: oh! and that aliexpress tester is only 4 lines(usb2.0 basically)… usb 3.0 in type c is 24 pins… You’re not testing jack shit on that aliexpress. The device I linked will actually map the pins in the cable and will find you breaks as well.