Update on this: I’ve since been trying out Lawnchair. It’s pretty good. Definitely something I would suggest to someone to try out for themselves.
go $fsck yourself
My username is a wordplay on the Linux command filesystem check: fsck.
- 1 Post
- 133 Comments
Isn’t the icons an aspect of the launcher?
I have not used it yet, but everyone seems to choose Lawnchair for their FOSS launcher.

 21·8 hours ago
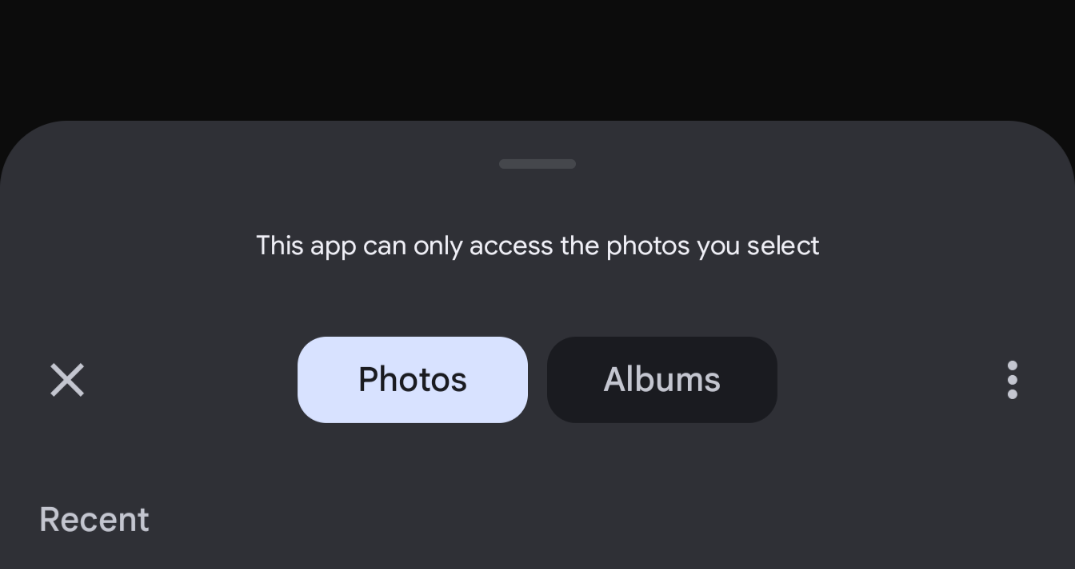
21·8 hours agoIn the media select window I see the ability to select from other apps:
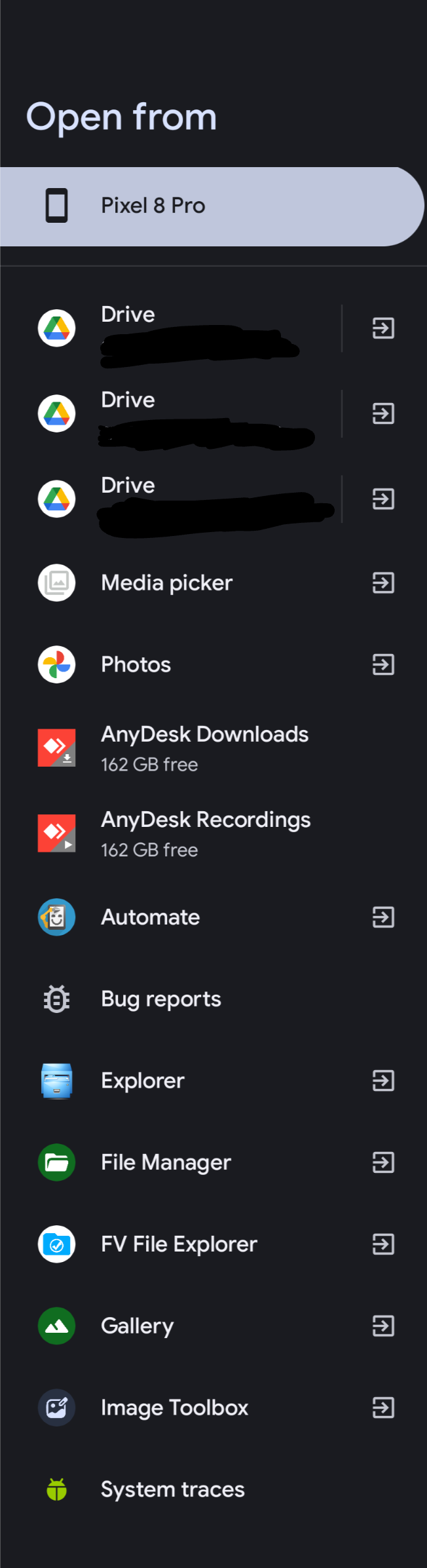
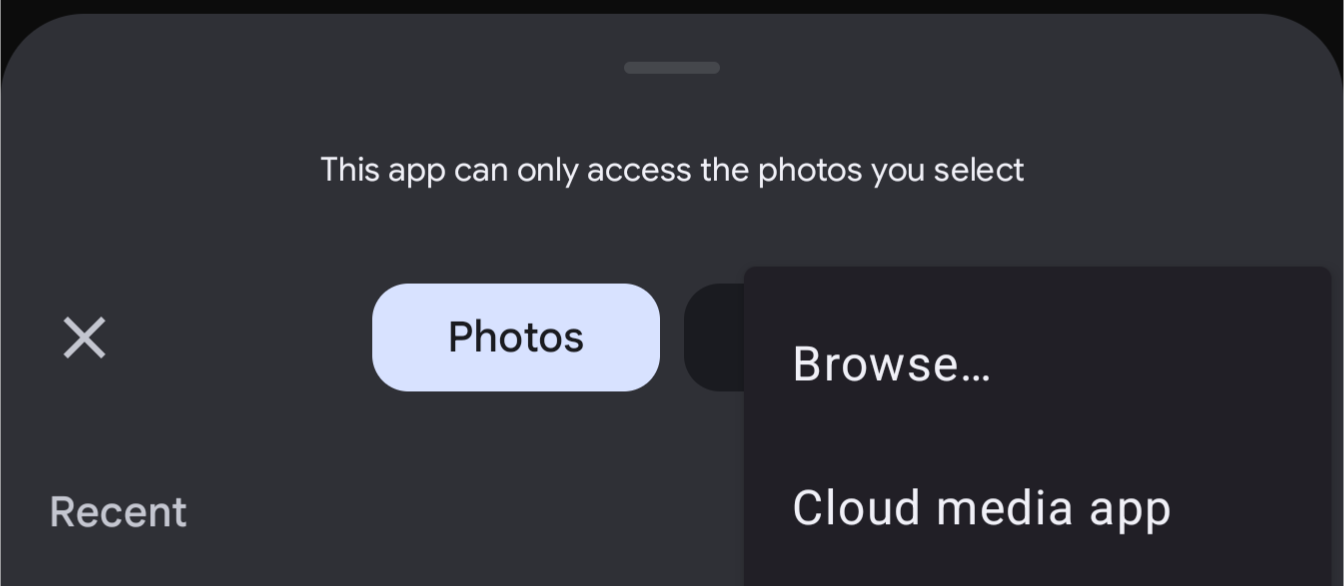
I do have to get there by selecting “browse” from the three dots menu

 1·1 day ago
1·1 day agoI am trying to avoid saving the image and only use the clipboard.

 1·1 day ago
1·1 day agoImgur was only an example. I don’t want to use imgur’s app and there are other websites or apps that I would like to upload to that do not work in that way.
I just want to be able to select an image from my clipboard when an app wants me to select an image from my phone.

 11·1 day ago
11·1 day agoI’m not trying to share the image, I’m trying to upload the image.

 1·1 day ago
1·1 day agoYou mean sharing a link to the URL?

 11·2 days ago
11·2 days agoAny considerations within this list?
https://github.com/awesome-selfhosted/awesome-selfhosted#calendar--contacts

 5·4 days ago
5·4 days agoThanks for the info from your experience
I’m not sure why you see it as a single incident. It was a series of choices—actions—that outline his overall behavior. I don’t see how a person who shows no empathy towards others, particularly from a position of ‘power’ over them, then refuses to acknowledge their poor behavior should get any empathy themselves.
It has always been a very easy option, if he wanted, to ameliorate the situation himself. Instead he chose to stick to his choices multiple times.
You’re not wrong that it could be considered taking the high road to never bring it up. However, too often do people abuse that expectation to avoid consequences and just continue their behaviors. Without acknowledging their own actions there is no evidence that this is just not their own standard of behavior.
He showed everyone here who he really is. There’s no reason to just forget his real self when people keep posting links to his generic gaming blog site instead of the actual source of information.
Very succinct and includes 99% of the situation. Thanks, and well done.
Only things I would add would be: Being a moderator on lemmy and not knowing that modlogs are public is baffling. That alone really outlines the fact he was unqualified for the role.
And that it seems pretty obvious the comments were only deleted by him to hide his own. He had already shown an inability to be measured and collected, as well as a poor understanding of the platform from a moderation perspective. Then, his clear disregard for the only rule for the community by lashing out at something that could have been more easily dismissed entirely. He should have just deleted the comment without a response. My mildly stupid comment just did not deserve that kind of reaction.
It all serves as solid evidence that he was willing to abuse his mod role for something so minor, and a person like that wouldn’t stop there.
The real cherry on top is how pathetic it is to go to mastodon to complain about the public mod logs on lemmy.
The owner of gamingonlinux? The same guy was a mod on the !linux_gaming@lemmy.ml community until they were caught abusing their moderator powers? Who then deleted their account and complained on mastodon that it’s stupid design that mod logs are public? That one? [Screenshot]

 61·10 days ago
61·10 days agoYou think the average person understands email?

 41·17 days ago
41·17 days agoSince you’re going to childishly talk about me and infer something that is entirely false, I’m going to step in here.
First, you claim it’s “a convenient shorthand”, except “middleman” is far shorter than “man-in-the-middle”. So that argument is entirely false.
Next, “nothing that I wrote misrepresents the situation”? You literally linked the Wikipedia article for “Man in the middle attack”, but conveniently left out the word “attack” both when referring to it and in the link itself which redirected to the actual Wiki page https://en.wikipedia.org/wiki/Man-in-the-middle_attack.
You are clearly intentionally misrepresenting the subject in order to frame things to suit your narrative. That’s not just a claim out of nowhere, I provided evidence to support this.
And get out of here with your pathetic “like most of my colleagues” pretentious attitude.

 51·18 days ago
51·18 days agoomg that bar that kicked me out for being a belligerent asshole has stopped being a bar and now they’ve become the police. They have too much power!

 61·18 days ago
61·18 days agoOookay. I wasn’t actually claiming you were talking out of your ass. I was explaining that without backing up your claims with information, then that would be the conclusion.
Since you are refusing to do so, and since you seemed to identify with that, along with clearly conflating the two terms to suit your narrative. I can now say it’s safe to assume that you are talking out of your ass. Especially considering the first part of your response reeks of arrogance.

 9·18 days ago
9·18 days agoYou’re conflating MitM, which is specifically defined as an attack, with the concept of a middleman. You acknowledge that it’s not an attack, even:
It just means it’s not a man-in-the-middle attack.
The other things you’re describing are also framed specifically in a way that makes Cloudflare seem like some sort of bad actor out of the norm.
You say users have no choice in using Cloudflare. Yeah, the party that runs the service/website/whatever decides what services they use to serve their content. Nothing special there. If you are against Amazon then users have no choice but to use them when the other side chooses to use their services, or any other service provider which includes the ones you like. Similarly, users would have to resolve DNS records to determine what services they are connecting to.
You also don’t have to use Cloudflare’s proxy. You can just use them for DNS record management. You can use different SSL settings that allow an unencrypted connection between Cloudflare and the server, or you can enforce strict SSL policies where it is encrypted end-to-end.
You’re going to have to prove any of your claims, or else I am just going to assume you’re talking out of your ass. Particularly because you’re clearly misunderstanding what a MitM is, or you’re intentionally misusing it.
-edited formatting-

 171·18 days ago
171·18 days agoDid you even look at the article or did you see “Cloud flare” in the title and immediately grabbed your pitchfork?
The article is outlining a situation where Cloudflare is advocating to maintain privacy.

Yeah. This is tempting me to set up an android dev environment myself. Never done any android dev besides React Native.